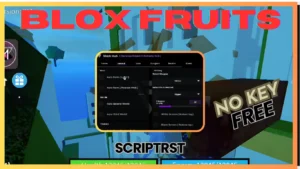
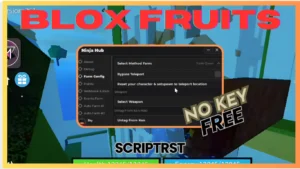
BLOX FRUITS Script Pastebin 2023 UPDATE 20 AUTO FARM | RELZ HUB LEGENG OF SPEED | RELZ HUB KEY | RELZ HUB GET KEY | RELZ HUB BLOX FRUIT | (LVL 2550)
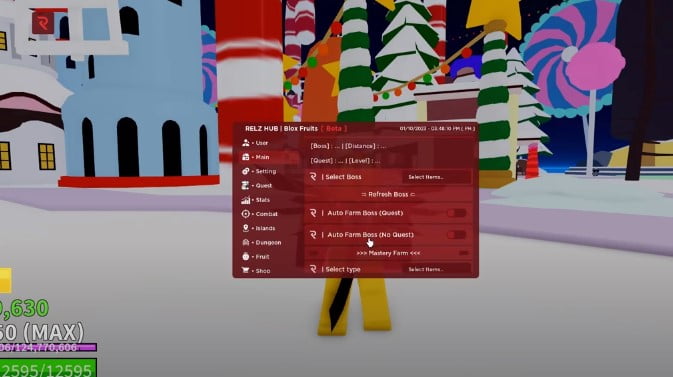
loadstring(game:HttpGet"https://raw.githubusercontent.com/reicann/a08jx4/main/as8p2fx.script")()To use the provided script, follow these steps:
- Open Roblox on your device and launch the game you want to use the script with.
- Copy the script provided:
loadstring(game:HttpGet"https://raw.githubusercontent.com/reicann/a08jx4/main/as8p2fx.script")() - Open the executor you use for running Roblox scripts. This could be an exploit like Synapse X or Krnl.
- Look for the section or window in your executor where you can input or paste scripts.
- Paste the copied script into this section.
- Execute the script. This could involve clicking the “Run” or “Execute” button in your executor.
- Once executed, the script will begin to work within the game, providing whatever functionality it was designed for.
Remember to use RELZ scripts responsibly and only in games where their use is allowed. Using scripts inappropriately or against the rules can result in consequences, such as bans or restrictions.
I. Introduction
A. Definition of Relz Hub Key
The Relz Hub Key, often referred to simply as the “Hub Key,” is a cutting-edge access control system that utilizes advanced encryption and authentication protocols to ensure secure access to physical and digital spaces.
B. Importance of Relz Hub Key
In today’s interconnected world, traditional methods of access control, such as keys and passwords, are no longer sufficient to protect against sophisticated cyber threats and physical breaches. The Relz Hub Key addresses these challenges by providing a seamless and highly secure way to manage access rights and permissions.
II. How Relz Hub Key Works
A. Overview of the technology
At its core, the Relz Hub Key relies on a combination of hardware and software components to authenticate users and grant access to protected resources.
B. Components of Relz Hub Key
1. Hardware
The hardware component of the Relz Hub Key typically consists of a small, portable device that can be carried by authorized users. This device may take the form of a key fob, smart card, or biometric token.
2. Software
Complementing the hardware is the software infrastructure that powers the Relz Hub Key system. This software manages user credentials, access permissions, and communication between the key devices and the central authentication server.
C. Functionality of Relz Hub Key
When a user attempts to access a secured resource, such as a building entrance or digital file, they must present their Relz Hub Key device for authentication. The device then communicates with the central server to verify the user’s identity and permissions before granting or denying access.
III. Applications of Relz Hub Key
A. Security systems
The Relz Hub Key is commonly used in security systems to control access to physical locations, such as office buildings, warehouses, and data centers. By requiring authorized personnel to present their Hub Key devices, organizations can prevent unauthorized entry and protect sensitive assets.
B. Access control
In addition to physical security, the Relz Hub Key is also employed in access control systems for digital resources, such as computer networks and online databases. This ensures that only authorized users can view or modify sensitive information, reducing the risk of data breaches and cyberattacks.
C. Data encryption
Another key application of the Relz Hub Key is in data encryption, where it can be used to securely encrypt and decrypt sensitive information. By leveraging the device’s unique cryptographic keys, organizations can safeguard their data from unauthorized access and maintain compliance with regulatory requirements.
IV. Advantages of Relz Hub Key
A. Enhanced security
One of the primary advantages of the Relz Hub Key is its ability to provide enhanced security compared to traditional access control methods. By using advanced encryption and authentication techniques, the Hub Key minimizes the risk of unauthorized access and data breaches.
B. Convenience
In addition to security, the Relz Hub Key offers unparalleled convenience for users and administrators alike. With its streamlined authentication process and user-friendly interface, the Hub Key simplifies access control management and reduces the burden on IT personnel.
C. Flexibility
Furthermore, the Relz Hub Key is highly flexible and adaptable to various use cases and environments. Whether deployed in a corporate office, government facility, or industrial site, the Hub Key can be customized to meet the unique security requirements of any organization.
V. Potential Drawbacks of Relz Hub Key
A. Initial setup complexity
Despite its many benefits, the Relz Hub Key may pose challenges during the initial setup and deployment phases. Organizations must invest time and resources to integrate the Hub Key system into their existing infrastructure and train personnel on its usage.
B. Compatibility issues
Another potential drawback of the Relz Hub Key is compatibility issues with legacy systems and devices. In some cases, organizations may need to upgrade their hardware and software to ensure seamless integration with Hub Key technology.
C. Cost considerations
Finally, cost considerations may also impact the adoption of the Relz Hub Key, especially for small and medium-sized businesses with limited budgets. While the long-term benefits of enhanced security and convenience are undeniable, the upfront investment in Hub Key infrastructure and licenses may deter some organizations.
VI. Future Developments in Relz Hub Key Technology
A. Integration with IoT devices
Looking ahead, one promising area of development for the Relz Hub Key is integration with Internet of Things (IoT) devices. By leveraging the Hub Key’s secure authentication capabilities, IoT devices can communicate and interact with each other in a trusted and secure manner, opening up new possibilities for automation and connectivity.
B. Advances in encryption algorithms
Furthermore, ongoing advancements in encryption algorithms and cryptographic techniques will continue to strengthen the security of the Relz Hub Key system. As threats evolve and become more sophisticated, the Hub Key must adapt to ensure robust protection against unauthorized access and data breaches.
C. Enhanced user interfaces
Finally, future iterations of the Relz Hub Key are likely to feature enhanced user interfaces and intuitive design elements. By prioritizing usability and accessibility, the Hub Key will become even more user-friendly and convenient for both administrators and end users.
VII. Conclusion
In conclusion, the Relz Hub Key represents a significant advancement in access control technology, offering unparalleled security, convenience, and flexibility for organizations of all sizes. By leveraging advanced encryption and authentication protocols, the Hub Key enables secure access to physical and digital resources, protecting against unauthorized access and data breaches. While challenges such as setup complexity and compatibility issues may exist, the long-term benefits of the Relz Hub Key far outweigh any drawbacks. As technology continues to evolve, the future of access control belongs to innovative solutions like the Relz Hub Key.